From Proof-of-Stake to Eigenlayer restaking and liquid restaking tokens like ynETH and ynLSD.
We are the YieldNest Risk Team, an independent risk and research firm operated by Llama Risk. Our work serves as a public good directed toward the YieldNest DAO for the purpose to assist in AVS onboarding decisions, but may be useful for anyone interested in liquid restaking or the study of the nascent AVS ecosystem.
#The Road to EigenLayer
In September 2022, Ethereum abandoned its long-time consensus algorithm — Proof-of-Work — for a new one called Proof-of-Stake. This upgrade marked a new era for Ethereum, with an estimated 99.9% reduction in energy consumption of the network, as well as a new paradigm where the economic policy of Ethereum is on autopilot.
In this first blog series, we go back to the origin of the Ethereum consensus algorithm, Proof-of-Work, and the transition to Proof-of-Stake. We glimpse at what it implies for those taking part in securing the network, and how it changed the economic policy of Ethereum forever. Then, we introduce the technological innovations that took place to facilitate Ethereum staking through the EVM with smart contracts and how it improves its capital efficiency — namely liquid staking. Finally, we introduce re-staking with EigenLayer and its corollary, liquid re-staking, with the advent of liquid re-staking tokens like ynETH and ynLSD from YieldNest.
#Proof-of-Work
Proof-of-Work is the consensus algorithm that provided economic security to most cryptocurrencies — Bitcoin and Ethereum included — since their inception. For a cryptocurrency to remain secure, it must be such that the cost of an attack is greater than the benefit one would get from such attack. Proof-of-Work provides a simple yet powerful answer to this problem. Between each block, miners compete in a race to find an answer to a cryptographic challenge that is computationally hard.
Consider a hashing function f(x) = y such that computing f(y) is easy, but finding x from y is impossible. This property of f is called pre-image resistance, and can be understood as a one way function. At a fundamental level, it is due to the fact that the hashing function f destroys information about x in the process. Based on this mathematical consideration, an example of a Proof-of-Work challenge ressembles the following: given a pre-image resistant hash function f, find x such that the hash f(x) has a specific random string prefix. Because such x cannot be guessed, a miner has no other solution than to bruteforce a solution — meaning that they must try as many x values as possible until they find one whose hash f(x) has the required prefix. Now, the longer the prefix one must match, the harder it is to find a solution. Therefore, a parameter called the difficulty will automatically change the length of the prefix such that a solution will be found by the network — on average every 13 seconds for Ethereum — a duration also known as the block time.
In practice, Proof-of-Work algorithms — like EthHash for Ethereum — vary in their technical implementation, but they all prove that a time-consuming and power intensive work was done. Those algorithms have two implications. First, the probability to mine the next block is proportional to one's share of the total hashrate of the network, and therefore to its mining capital. Second, the oldest a block, the more expensive it becomes to rewrite history up to that block. Since one would have to compute PoW solutions for the hash of each block between now and the target block.
Simplified representation of PoW
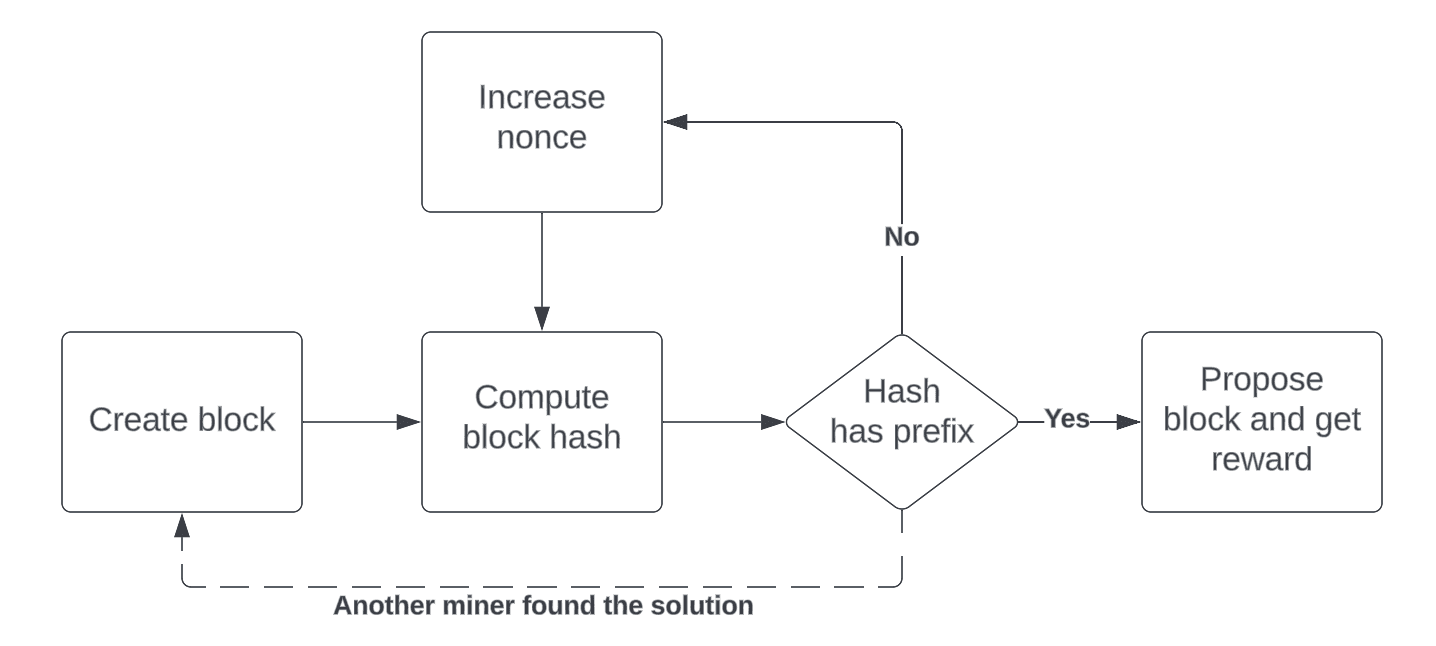
Proof-of-Work is performed by specialized computing hardware that is both expensive to acquire and consumes a lot of electricity. Attacking the network requires one to control more than 51% of network's hash rate, which would imply a gigantic investment that far outweighs the benefit one would get from doing so.
#Proof-of-Stake, a new Era
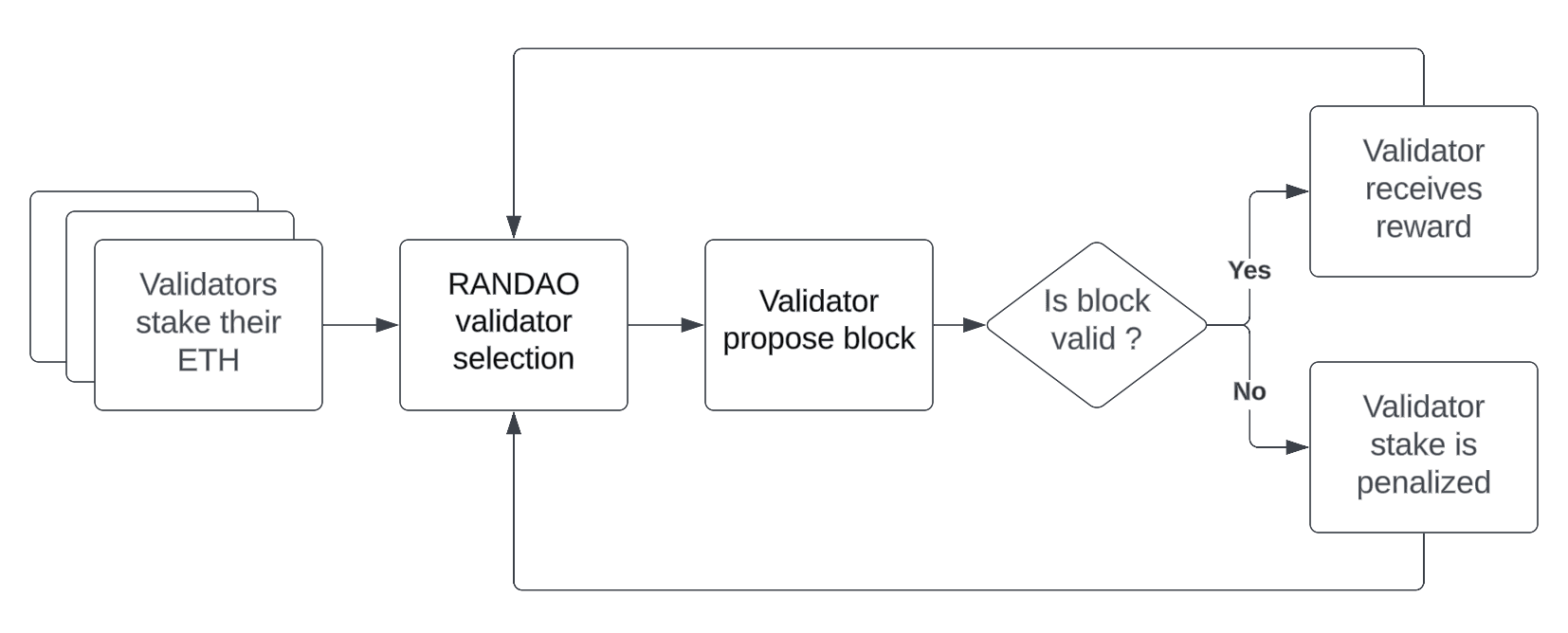
Since its inception in 2008, the electricity consumption of PoW chains has continued to increase until it reached that of small developed countries. Although some might argue that the cost was comparatively worth it compared to the traditional financial system, another promising consensus algorithm was being developed — Proof-of-Stake. With it, the security of the chain is no longer enforced by miners competing using expensive hardware and energy costs, but by validators that must attest to the correct chain's state, at the risk of losing part of an ETH bond that they must provide.
32 ETH is currently required for one to create a validator on Ethereum. If it fulfills its duty, a validator is rewarded with a yield on its staked ETH — around 4%, depending on the total number of validators on the network. However, if a validator behaves incorrectly, then it is punished by losing part of its stake. To prevent some specific attacks on the consensus, new validators must go through an entry queue, and exited validators must go through an exit queue. Each has a rate limit, meaning that depending on global demand from entering or exiting the Ethereum consensus, a validator could spend anywhere from a day to several months inside one of one of these queues. Because it won't be earning rewards duiring that time, this represents both an availability and liquidity risk for stakers. Current queue conditions can be monitored on validatorqueue.com .
Simplified representation of PoS
We now delve deeper into some of the penalties validators can potentially suffer from. They can be divided into two main types: failing to attest to the state of the chain, or lying about the state of the chain.
#Attestation failure
Attestation failure can be the result of either offline validators or late attestations due to network or computational degradations. Failure to attest to the state of the chain at each block will result in a penalty that approximately equals what a validator would have gained if it were attesting correctly. Therefore, it is not the kind of penalty that would prevent one from sleeping soundly.
The Ethereum network is fairly robust to an attestation rate of 95% or even 90%, although ultimately everyone benefits from keeping this value as high as possible — and that is because sharks are looming not far below. Indeed, things get dramatic fast if the attestation rate gets lower than 66% for longer than 4 epochs, in which case the chain would fail to finalize. To incentivize validators to come back online, an inactivity leak penalty comes into play, with a factor that grows quadratically over time. This article might be of interest to those who would want to delve deeper into the math involved. The goal of this penalty is twofold. First, it incentivizes validators to come back online as soon as possible because of its quadratic nature. Second, it bleeds the stake of offline validators until their share of the network goes below the 33% threshold, in which case the chain would be able to finalize again and the inactivity leak would stop.
#Slashable offense
A slashable offense is much more damaging and serious than a sporadic attestation failure. It happens when a validator is deemed to be actively trying to cheat and corrupt the chain, as in the following situations:
-
Two blocks are proposed and signed in the same slot.
-
Attesting to a block that forks the history.
-
Attesting to two different blocks in the same slot.
In practice, only offense number (1) could be the result of an inadvertent but honest validator, and can easily be produced by running two instances of a validator process using the same validator key. Proper knowledge and attention while managing staking infrastructure is enough to prevent this from happening. However, offenses (2) and (3) can only be the result of a faulty consensus client or of a malicious consensus client implementation — one that is designed to cheat.
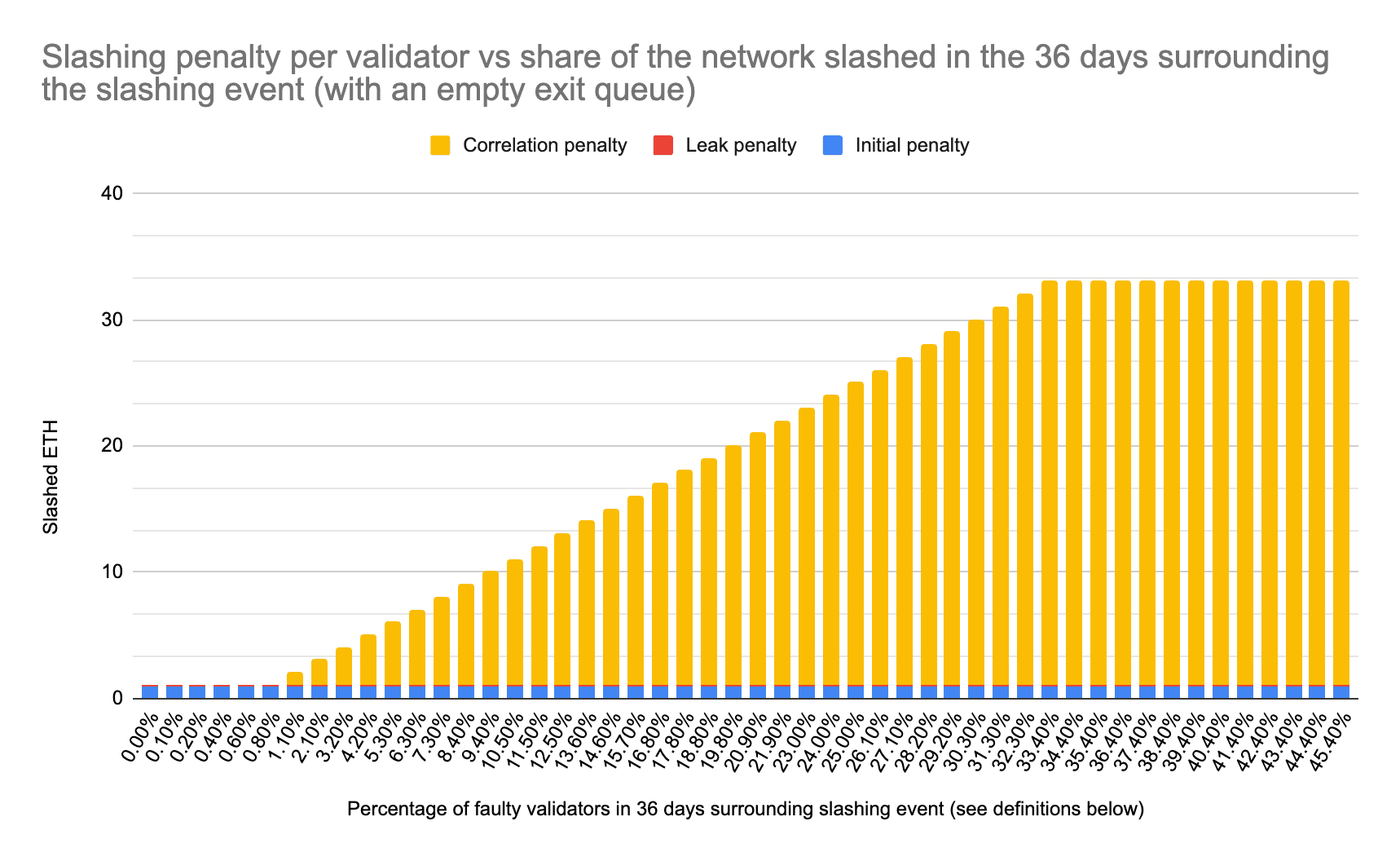
Source: LiquidCollective article (13-05-24)
The penalty for a slashable offense starts at approximately 1 ETH, and gradually increases up to 100% of the stake proportionately to the share of validators that were slashed during the last 36 days, up to 33% of the total number of validators. This gradual increase in the slashing penalty is called the correlation penalty. In addition to losing capital, the validator is exited from the beacon chain and enters the exit queue. In that queue, the validator will continue to suffer from another penalty called the leak penalty until it fully exits the queue.
It is important to note that, although a cheating validator might not have its stake fully slashed right away, it might lose more or even everything regardless of the initial slashed amount because of the length of the exit queue. Indeed, if the exit queue is particularly long — up to several months in the worst cases — its stake will fully bleed before exiting it.
#An economic policy on autopilot
The transition to Proof-of-Stake, together with the previously deployed EIP-1559 upgrade, marked the advent of a new economic policy for Ethereum. Previously with Proof-of-Work, the circulating supply of ETH was inflating at a fixed rate of 3.1% APY. With both EIP-1559 and Proof-of-Stake, the circulating supply is influenced by two variables — the gas usage and the number of validators. With EIP-1559, part of the transaction fee is burned, which reduces the supply of ETH proportionately to the gas price. With Proof-of-Stake, validators are now rewarded with both part of the gas fee paid by users and by ETH emissions. The greater the number of validators that are securing the consensus layer, the more ETH is emitted to reward them (although this reward gets marginally lower as the number of validator increases).
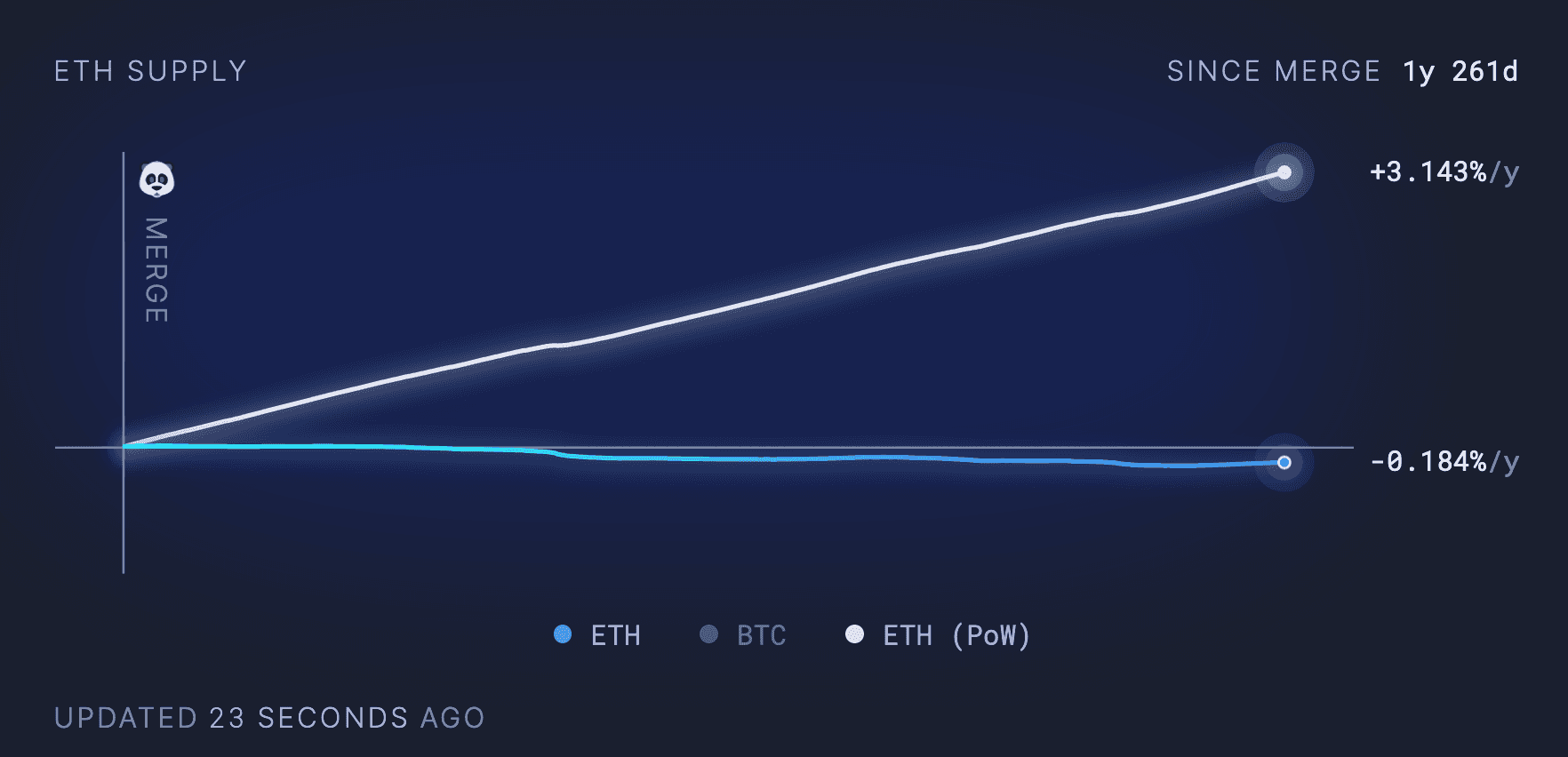
Source: ultrasound.money (01-06-24)
Two opposing forces are inviting more of each other and ultimately balance themselves. More transaction fees increases the validators' yield, hence incentivizing more of them to secure the chain, but it also reduces the demand for block space as the chain becomes too expensive. On the other hand, lower transaction fees reduce the validators' yield to levels that are no longer competitive on the market, hence reducing the supply of validators, but it also makes the chain cheaper to use, thus enabling more use cases. We obtain an economic system that has a dynamic, global equilibrium. Gone is the time of quarterly meetings by bureaucratic elites to decide how much money to print! The economic policy is on autopilot.
There is a case to make for considering staked ETH as a bond. Indeed, the staked ETH yield is the purest you could find on Ethereum, since it is the reward one gets for securing and enabling the network itself. Although bonds — especially government bonds — are commonly considered as being risk free, as we've seen previously, it is hardly the case for ETH staking: running a validator requires technical abilities to avoid penalties and turn a profit out of the operation. But if the Ethereum consensus breaks, so does all the financial infrastructure that is built on top of it — just like traditional bonds in the financial market. In that sense, the Ethereum staking yield can be understood as the lowest-risk yield of all on decentralized markets, hence deserving the title of internet bond.
#Liquid staking
Participating in Proof-of-Stake is not a simple endeavor, as it requires:
-
At least 600$ to acquire the hardware necessary to operate a full node.
-
Technical abilities to maintain a high uptime and avoid penalties.
-
32 ETH of capital required and locked in a capital-inefficient way.
Liquid staking protocols aim to solve one or more of these constraints. They essentially act as intermediaries between the stakers and the beacon chain by abstracting the staking process through smart contracts. It generally works as follows: one deposits any amount of ETH in a contract operated by a third party. Once enough ETH is deposited, the third party starts one or more validators on the staker's behalf and maintain them. In exchange, liquid stakers are given a liquid staking token (LST) that represents their stake, and that is composable accross DeFi. Either a repricing or a rebasing token, it automatically accrues in value proportionately to the rewards accumulated by the underlying validators. The third-party takes a cut — often 10% — of the rewards accumulated by the validators.
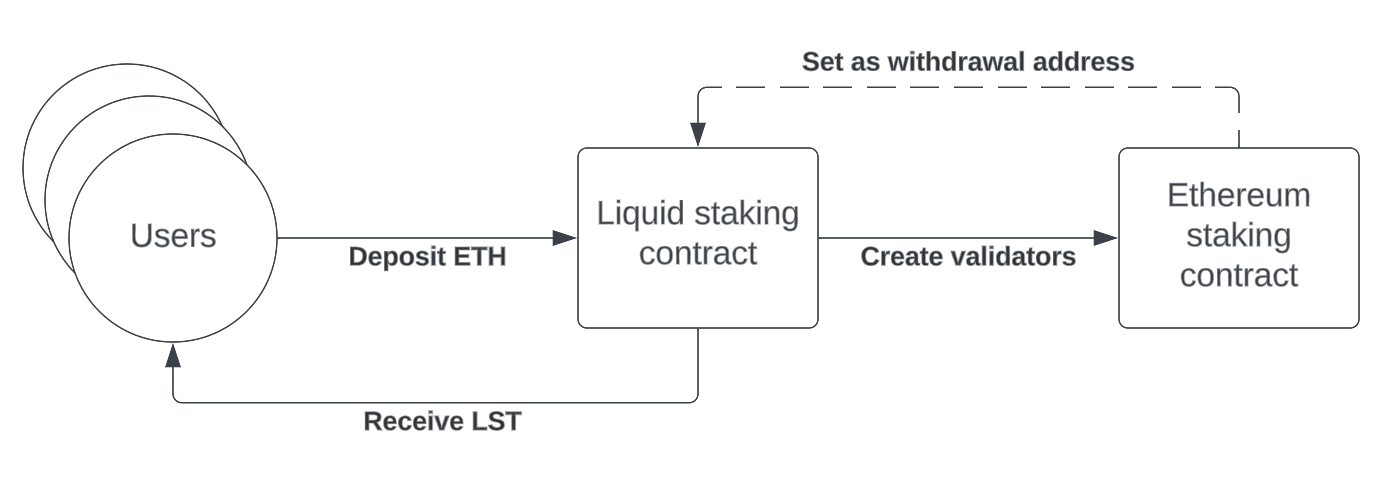
Since the Ethereum Merge — namely the transition event that replaced Proof-of-Work with Proof-of-Stake — a large variety of liquid staking solutions have emerged. The first and most used one is LiDo, a permissioned liquid staking solution where one can mint stETH in exchange for ETH. Other liquid staking protocols have tried to compete and improve on other aspects by being permissionless and by allowing anyone to run validators on behalf of others, like RocketPool or StakeWise.
It is important to note that liquid staking protocols vary in terms of risk and reward profiles. If their proposed yield rarely deviate much from each others, they inevitably add risks related to smart contracts, as well as potential centralization risks related to their technical implementation and counterparties. The soft peg of LSTs to ETH is also at risk due to the entry and exit queues of the Ethereum consensus, which can slow down arbitration opportunities. Therefore, solo staking will always be less risky than liquid staking.
#Understanding Regulations
Proof-of-Stake protocols have caught the attention of regulators worldwide, with many still grappling with its core principles and how to integrate it into existing legal frameworks. In some jurisdictions, regulators have attempted to classify staking within the realms of traditional finance, equating it with regulated financial activities like securities offerings. Conversely, in other regions, industry stakeholders have successfully communicated that staking is a voluntary process where crypto asset holders lock up their assets to support transaction validation on a blockchain network. Below are some of the diverse regulatory approaches to staking in key countries striving to lead the crypto economy.
-
United Kingdom - HM Treasury has introduced a detailed taxonomy for staking business models, distinguishing between solo staking, delegated staking, decentralized pooled staking, and centralized pooled staking. While no plan is made to ban staking, it acknowledges that intermediated activities — whether centralized or decentralized — pose risks to consumers. These activities include taking custody of and/or pooling crypto assets and issuing liquid tokens. Focused legislation addressing these risks is expected to be enacted this year.
-
Switzerland - Financial Market Supervisory Authority (FINMA) has assessed custodial staking and determined that certain models may be classified as bank deposits. If a custodian operates the validator nodes' technical infrastructure and holds both the withdrawal and validator keys, it must maintain exclusive control over the crypto assets, making them accessible to clients at all times. For outsourced validator operations, custodians must retain control over the assets.
-
Dubai - Virtual Asset Service Providers (VASPs) licensed by the Virtual Assets Regulatory Authority (VARA) may only offer staking through custody services if explicitly authorized by VARA. This authorization must be clearly stated in their license. VARA considers this form of staking part of the custody services provided by VASPs, requiring them to meet all related requirements on an ongoing basis.
-
Singapore - The Monetary Authority of Singapore (MAS) has taken a cautious approach towards centralized staking activities. It has restricted Digital Payment Token (DPT) service providers from facilitating the lending and staking of DPT tokens for retail customers, deeming these activities unsuitable for the general public. However, DPT service providers can continue offering lending and staking services to institutional and accredited investors.
#Re-staking
If ETH staking implies the bonding of ETH to secure the Ethereum consensus, ETH re-staking refers to the additional responsibility that an ETH staker can take to secure other decentralized applications. Enabled by EigenLayer, and still in its infancy, re-staking enables the efficient use of the economic security of Ethereum to secure other applications, including but not limited to:
-
Data Availability (DA) Layers
-
Decentralized sequencing
-
Coprocessors
-
Oracles
-
Bridges
Applications secured through re-staking are called Actively Validated Services (AVS), and are operated in a decentralized network by Operators. To learn more about AVS categorization, please look at our AVS categorization research. Restakers can decide to secure one or more AVS of their choice, either through a third-party Operator or themselves by taking on the responsibilities of an Operator. When registering to secure an AVS, a restaker must perform specific duties through an Operator. If they fail to perform them as expected, they will be subjected to additional penalties — that is on top of the penalty they are already be subjected to by securing the Ethereum consensus. In exchange for those additional responsibilities and risks, restakers are rewarded with additional yield on their staked ETH.
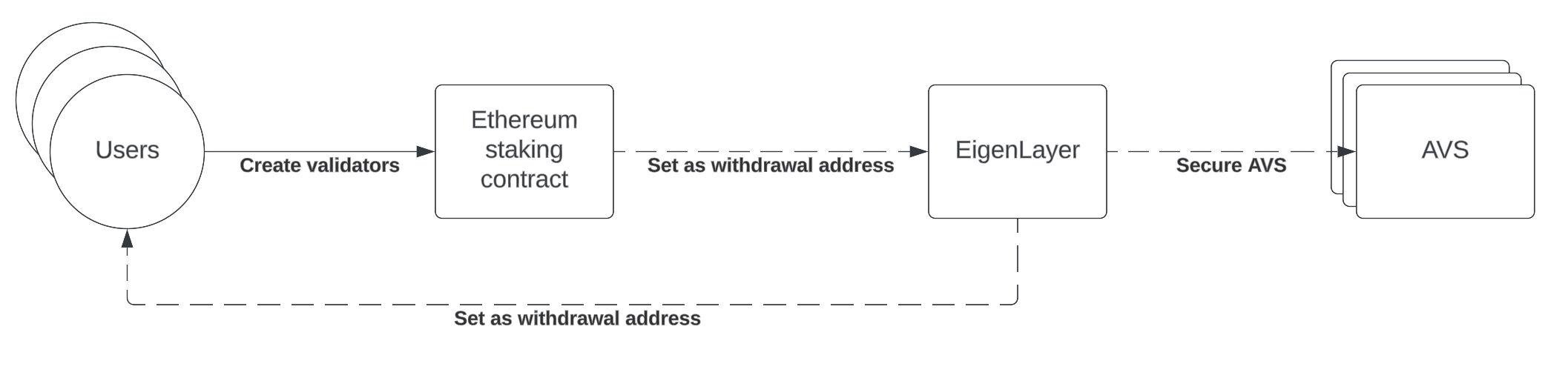
It is important to note that the duties of a restaker and the penalties it can be subjected to are specific to each AVS, and that the EigenLayer protocol itself only acts as an intermediary to enable a market where restakers, Operators, and AVSs can freely enter mutually beneficial relationships.
In practice, re-staking is available for both solo stakers and liquid stakers. Solo stakers would simply set their withdrawal address as an EigenLayer-controlled smart contract address, which will then add or remove rewards and penalties respectively — this is also known as native re-staking. Liquid stakers, however, would directly deposit their LSTs into EigenLayer. Whether or not a staker is restaking natively or through LSTs, another layer of smart contract dependencies inevitably adds risks related to security breaches and exploits.
#Toward liquid re-staking
Built upon the concept of LST is that of Liquid Re-staking Tokens (LRT). As one would expect, it allows re-stakers to mint a liquid token against ETH re-staked in EigenLayer. This re-staked ETH can be provided through either native staking or LSTs. We obtain a token whose yield is composed of both the Ethereum consensus yield and the yield added by each AVS secured by the re-staked ETH. Just like for LSTs, it is an ERC-20 token that can be composed with in DeFi and used as a yield bearing collateral.
Liquid Native Re-staking
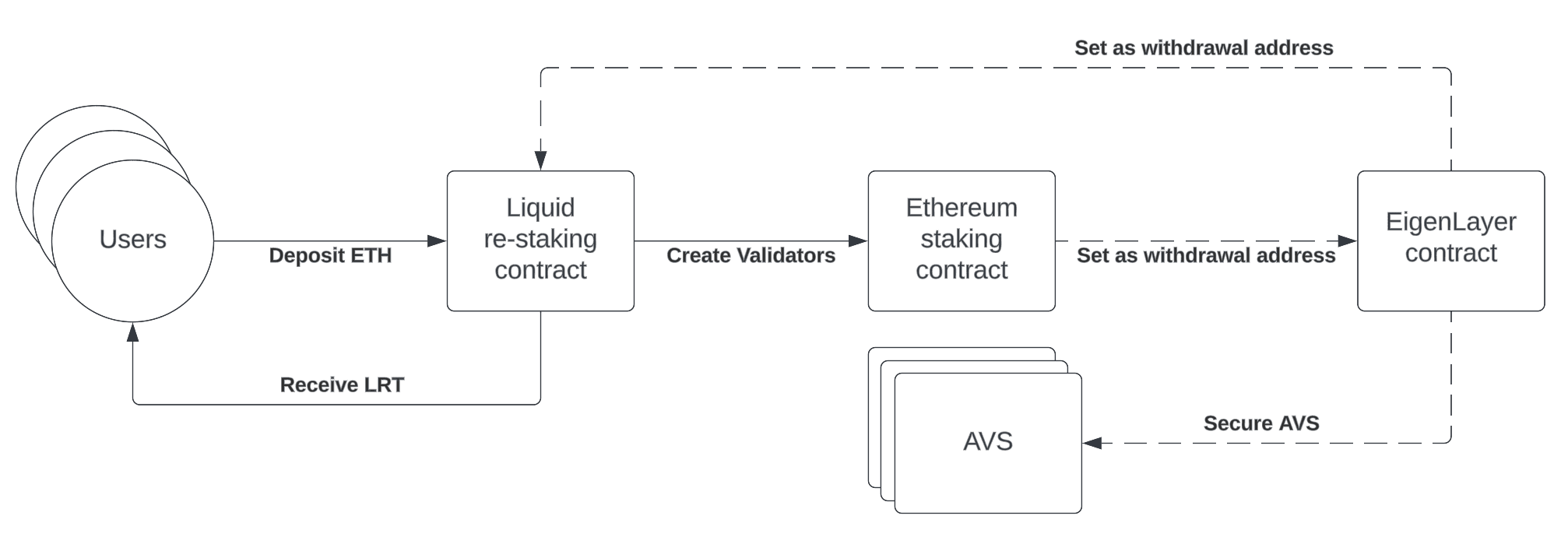
Liquid Native re-staking is similar to native re-staking, the only difference being that the liquid re-staking contract acts as an intermediary in order to liquify the stake of users and provide them with LRT tokens. At YieldNest, this is the purpose of the ynETH token that is now offering a 3.5% yield thanks to a curated basket of AVSs selected by our risk analysts.
Liquid LST Re-staking
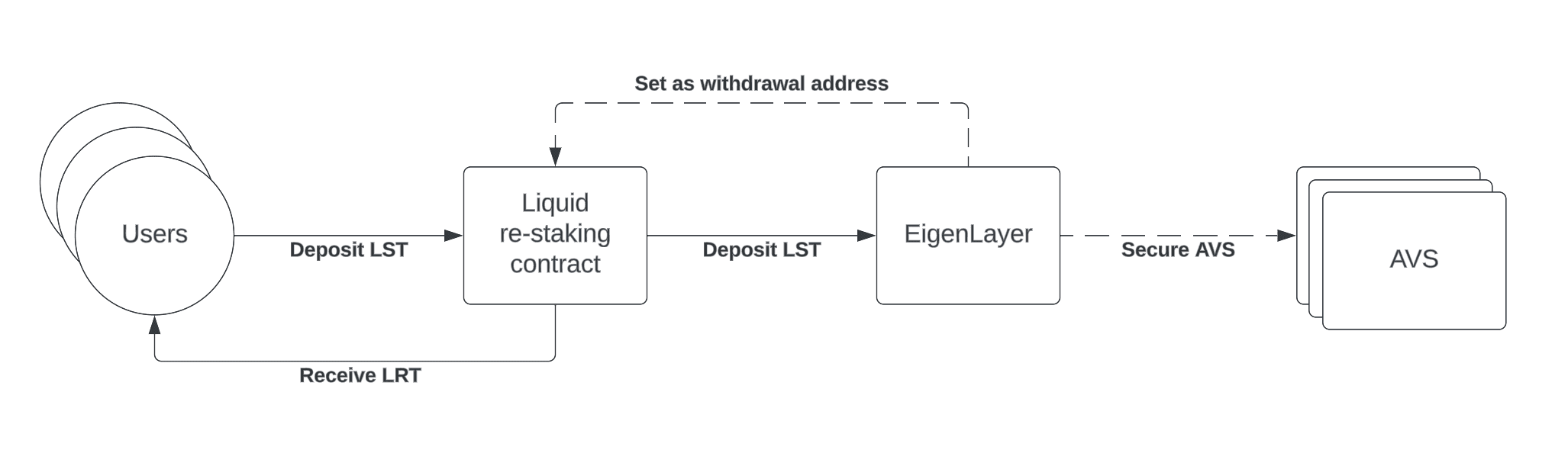
The second way to re-stake is to directly deposit a supported LST into a liquid re-staking protocol. LST re-staking has more smart contract and centralization risks compared to Liquid Native Re-staking because one must previously interact with a liquid staking protocol. The ynLSD LRT of YieldNest will soon be offered for stakers with LST tokens.
#Conclusion
Because it is up to the re-staker to select which AVS to onboard, a significant complexity arises from the ability to secure any subset of existing AVSs. The risk/reward profile of the LRT becomes the weighted sum of each AVS's risk/reward profile. Furthermore, to be liquified, re-staked ETH must go through yet another layer of smart contracts with corresponding potential risks. Therefore, to fully benefit from the possibilities offered by re-staking and the liquefaction of one's stake for composability accross DeFi, a careful multi-factorial analysis is needed.
In the next blog post of this series dedicated to LRTs, we will delve deeper into the functioning of EigenLayer and the different actors involved — namely re-stakers, AVSs and Operators. We will also gaze upon newly developed LRT protocols like YieldNest and see how we can better model the risk/reward profile of each AVS.