This research analyzes the LayerZero OFT standard managing $44 billion in cross-chain assets, evaluating risks from smart contracts, off-chain dependencies, and regulatory complexities.
The adoption of the LayerZero Omnichain Fungible Token (OFT) standard has consolidated across different networks and major DeFi protocols, bringing bridged asset amount to a total of $44B. Notably, within Aave alone, the biggest DeFi protocol by TVL, where total net deposits exceed $40 billion, assets using OFT account for approximately $7.4 billion in TVL, which is a considerable 18.5% share.
As exposure to OFT-powered assets continues to rise, it becomes increasingly important to clearly outline the architecture and associated risks of this token standard. This research explores the fundamental design of the OFT model and evaluates key risk dimensions, including smart contract vulnerabilities, price feed dependencies, external trust assumptions, and legal uncertainties, also comparing it with other bridge models.
#Summary
The LayerZero Omnichain Fungible Token (OFT) standard enables native cross-chain token representation through burn-and-mint or lock-and-mint mechanisms. While native OFTs offer seamless, canonical token representation across chains, they require issuer involvement to adopt the standard. Adapter-based OFTs, though, extend omnichain functionality to existing tokens without the need contract changes, however, are not a true canonical representation of the source token, introducing custodial and source-chain liveness risks for OFT backing via the adapter contract. Nonetheless, token issuers retain full administrative control over OFT contracts, reducing risks associated with third-party bridge custodianship.
While LayerZero’s immutable endpoints prevent disabling chain support, dependence on off-chain workers (DVNs and Executors) introduces dependency and oracle risks. Cross-chain message verification relies on configurable sets of Decentralized Verifier Networks (DVNs) and Executors, whose security depends on the diversity and reliability of chosen workers set, with varying cryptographic verification methods and potential collusion risks. Overall, OFTs reduce liquidity fragmentation and improve capital efficiency but inherit security dependencies from LayerZero’s messaging infrastructure, presenting low to moderate systemic risks depending on worker configuration.
From a legal standpoint, an OFT's classification is not uniform but mirrors the underlying token's function (e.g., utility, payment, or security) and varies by jurisdiction. This omnichain nature creates significant regulatory challenges, as the cross-chain architecture complicates jurisdiction-based supervision and the burn-and-mint mechanism raises novel questions about what constitutes issuance. Regulators are likely to scrutinize identifiable service providers in the stack—such as DVNs, oracles, and relayers—potentially classifying them as regulated entities like Virtual-Asset Service Providers. Furthermore, the issuer's administrative control over the OFT contract presents a point of centralization that attracts oversight, while the token's presence across multiple chains introduces risks from conflicting legal frameworks, smart contract liabilities, and data privacy obligations.
#1. Scale & Usage
As with most cross-chain activities, the usage of LayerZero's inter-chain messaging infrastructure is related to the underlying activities caried out in different chains, as well as broader market conditions. At the same time, the usage of LayerZero's solutions has varied greatly, reaching a peak in mid-2023, with a stabilization at lower levels over the years that followed. Currently, about 2M messages are being processed by the system, with overall minor growth in served networks.
The usage of the OFT mechanism over different networks is most notable on Ethereum, Arbitrum, Avalanche, Base, Gnosis, Optimism, Polygon, and other smaller, less mature networks. Since early 2022, ~150M cross-chain messages have already been delivered by LayerZero with a total bridged asset amount currently standing at $44B.
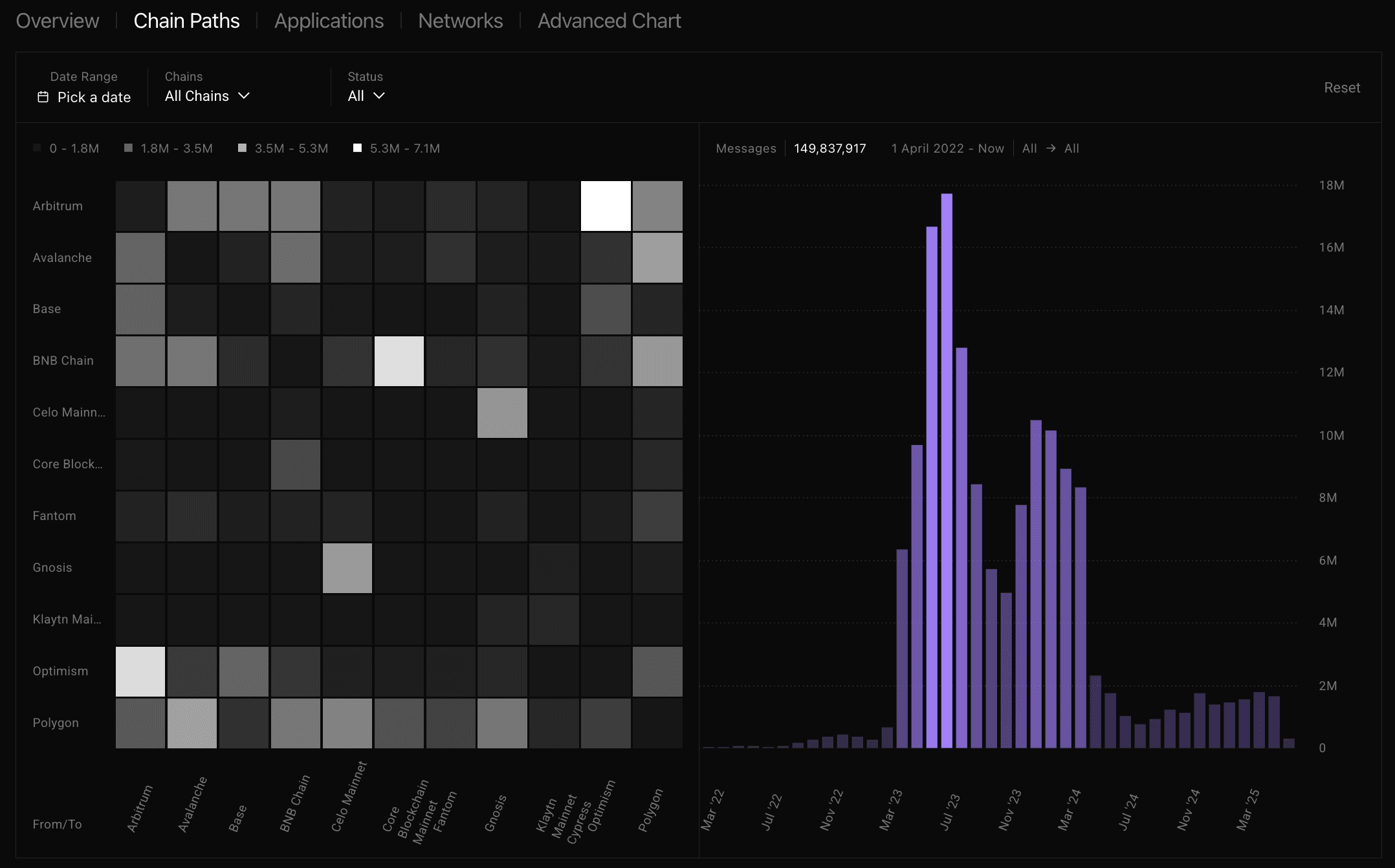
Source: LayerZero Analytics, June 7, 2025
Considering this scale, LayerZero remains one of the most actively used infrastructures in DeFi, standing among the top 3 based on the daily processed volume. The availability of LayerZero among numerours chains is also notable, as most contenders concentrate on a more limited set of chains to deploy their infrastructure.
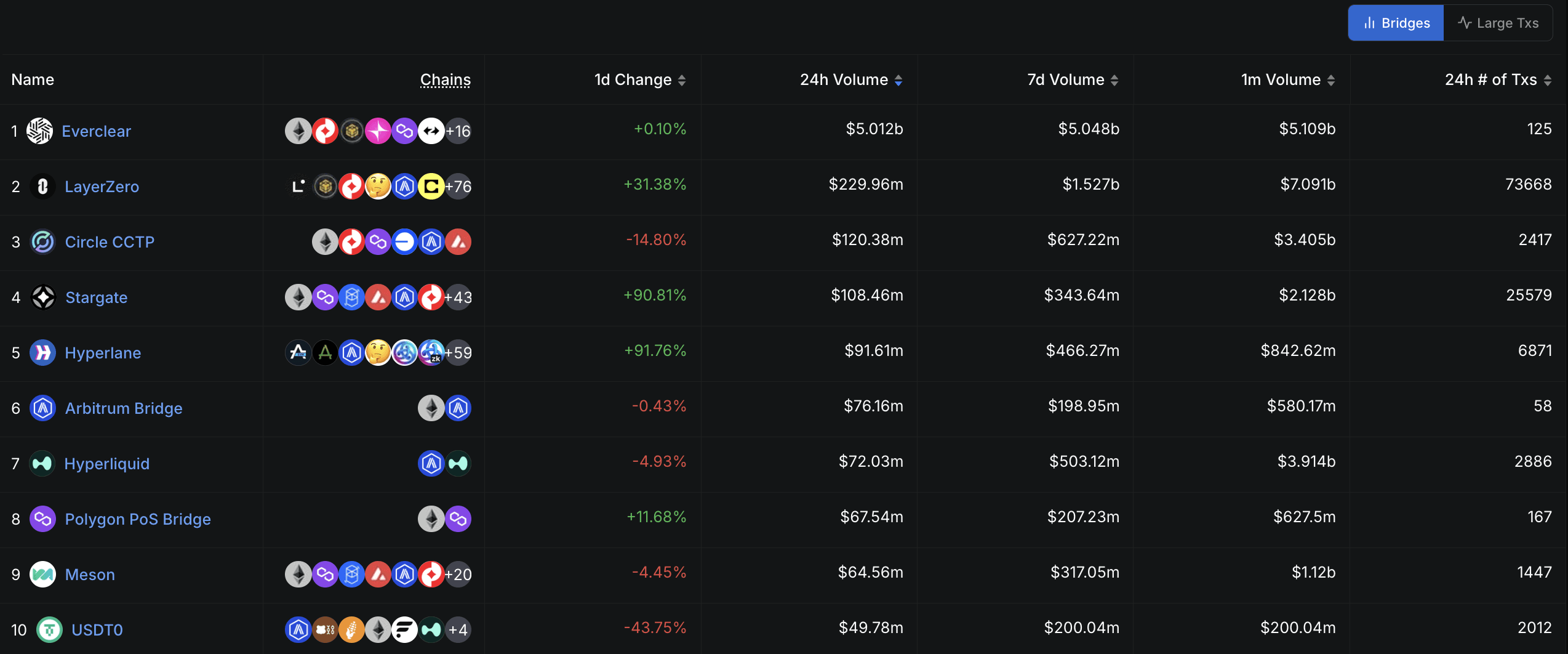
Source: DefiLlama, June 7, 2025
#2. System Design
Focusing on the inner-workings, OFT standard by LayerZero aims to create a native cross-chain token experience, eliminating the inter-chain interaction problems associated with traditional wrapped assets. In particular, OFTs are designed to:
-
Allow a token to exist natively across multiple blockchains without being "wrapped." This means that
TOKEN_Aon Ethereum is the same canonicalTOKEN_Aon Polygon, Arbitrum, and other supported chains, unlike wrapped versions such aswTOKEN_AorpolyTOKEN_A. -
Improve capital efficiency by preventing liquidity fragmentation caused by multiple wrapped variants of the same asset. Additionally, OFT cross-chain transfers only require gas fees, avoiding extra costs typically associated with wrapping, bridging, or slippage.
-
Provide token issuers with full control over their tokens across all chains. Project teams retain ownership and upgradability of token contracts, and can set custom parameters such as transfer fees to enable protocol-level revenue generation.
#2.1 High-Level Flow
The OFT standard extends fungible token standards like ERC20 by integrating LayerZero's messaging infrastructure to enable seamless token transfers across multiple blockchains. At its core, the LayerZero protocol establishes a messaging channel between sender and receiver smart contracts using source and destination endpoints deployed on each supported chain.
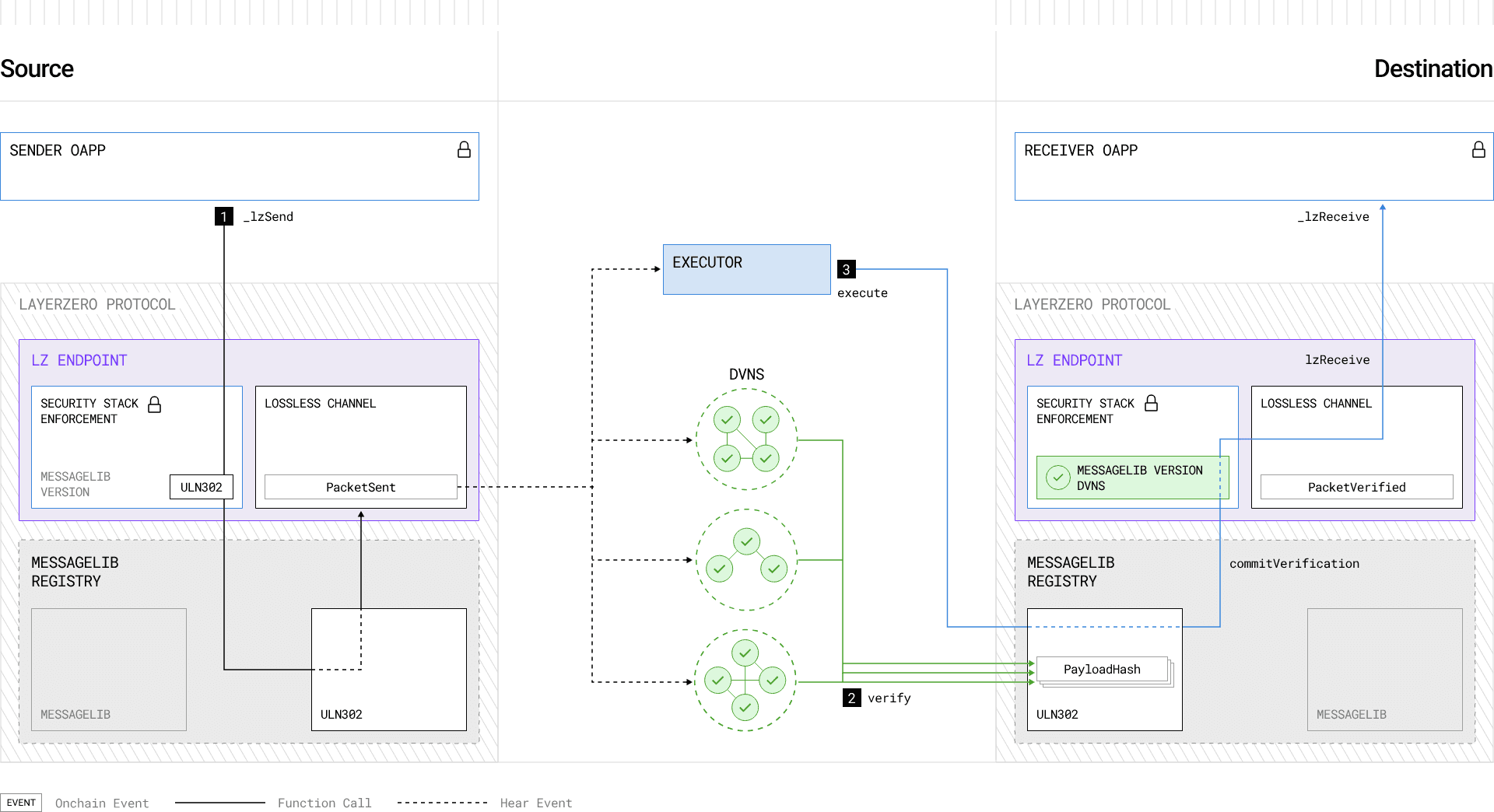
Source: LayerZero Cross-chain Messaging Architecture, LayerZero Docs
These LayerZero Endpoints act as immutable and permissionless protocol entry points for sending and receiving omnichain messages. When a transfer is initiated, the source endpoint emits a message packet as an event. This packet contains the source and destination endpoint IDs, sender and receiver addresses, and a message payload, together forming a unique messaging channel.
On the destination chain, the payload is verified using the configured Security Stack, which consists of a set of Decentralized Verifier Networks (DVNs) (discussed further in the Dependency Risk section). Once verified, the payload is passed to the receiver contract’s Message Library. Finally, an Executor contract calls the endpoint's exit function to deliver the payload to the receiver address.
#2.2 Dual Bridging Setup
OFTs operate using two primary models, each offering distinct strengths and trade-offs. The decision of which model to implement is guided by either strategic preference, based on the issuer's goals and token type, or by technical necessity when only one option is feasible.
#2.2.1 OFT Transfer (Burn-and-Mint)
The burn-and-mint mechanism is designed for both new, natively omnichain tokens and existing tokens whose issuers choose to adopt the OFT standard. This model maintains a constant total supply across all integrated chains, only altering the token's distribution between them. To achieve this, a project deploys a corresponding OFT contract (such as OFT.sol or OFTCore.sol) on each target blockchain. These contracts are then linked as peers through the LayerZero protocol to manage the cross-chain supply.
The OFT standard includes built-in methods to support composed calls, allowing messages to be passed along with the token transfer. In a typical flow, a message is sent from chain A to chain B, and upon receipt, the destination OFT contract can execute additional logic such as interacting with external contracts through a composed message chain (A → B1 → B2 → …), depending on application-specific requirements.
When a user initiates a token transfer from Chain A (source chain) to Chain B (destination chain):
-
The specified amount of tokens is burned on Chain A, and the OFT contract on Chain A sends a message to the corresponding OFT contract on Chain B using LayerZero. This message is validated and executed by the Workers.
-
The OFT contract on Chain B receives the validated message and mints an equivalent amount of tokens to the user's address on Chain B.

Source: LayerZero Docs
Positives: The token on Chain B is the exact same canonical asset as on Chain A, not a wrapped version, reducing fragmentation and user experience as they interact with the same token version across all chains, without the need to perform additional operations to convert the token versions.
Drawbacks: This is only feasible if the token issuer designs their token as an OFT or is willing and able to migrate their existing token to a burn/mint model. Meaning it's not suitable for existing, immutable tokens without issuer cooperation. For example, Tether created a separate token contract for USDT (namely USDT0) specifically to support omnichain functionality under this model.
Risk Assumptions: The integrity and liveness of LayerZero's messaging infrastructure, i.e., Workers (DVNs and Executors), and the integrity of OFT smart contracts. Most importantly, during the bridging operation asset's security becomes dependent on LayerZero's off-chain execution security.
#2.2.2 OFT Adapter (Lock-and-Mint)
Other option, the lock-and-mint mechanism is adopted for existing tokens (e.g., USDC, ETH) that cannot be natively burned and minted by a whitelisted third-party OFT contract. In this setup, a project deploys an OFTAdapter.sol contract on the chain where the original token exists (e.g., USDC on Ethereum). The adapter contract then holds the original tokens, which are effectively locked before being bridged. To then execute bridging, standard OFT contracts are employed on the destination chains, enabling to mint the same amount of the locked counterpart residing on the source chain.
When a user wants to transfer from Chain A (source chain) to Chain B (destination chain):
-
The user approves the OFTAdapter on Chain A to spend their original tokens using
ERC20.safeTransferFrom. -
The OFTAdapter locks the original tokens and sends a message to the OFT contract on Chain B through LayerZero.
-
The OFT contract on Chain B receives the message and mints an equivalent amount of OFT tokens to the user's address.
To transfer back from Chain B (destination chain) to Chain A (source chain):
-
The user calls
OFT.sendon the OFT contract on Chain B, which burns the OFT tokens. -
A message is sent via LayerZero to the OFTAdapter on Chain A.
-
The OFTAdapter receives the message, unlocks the original tokens, and transfers them to the user's address on Chain A.
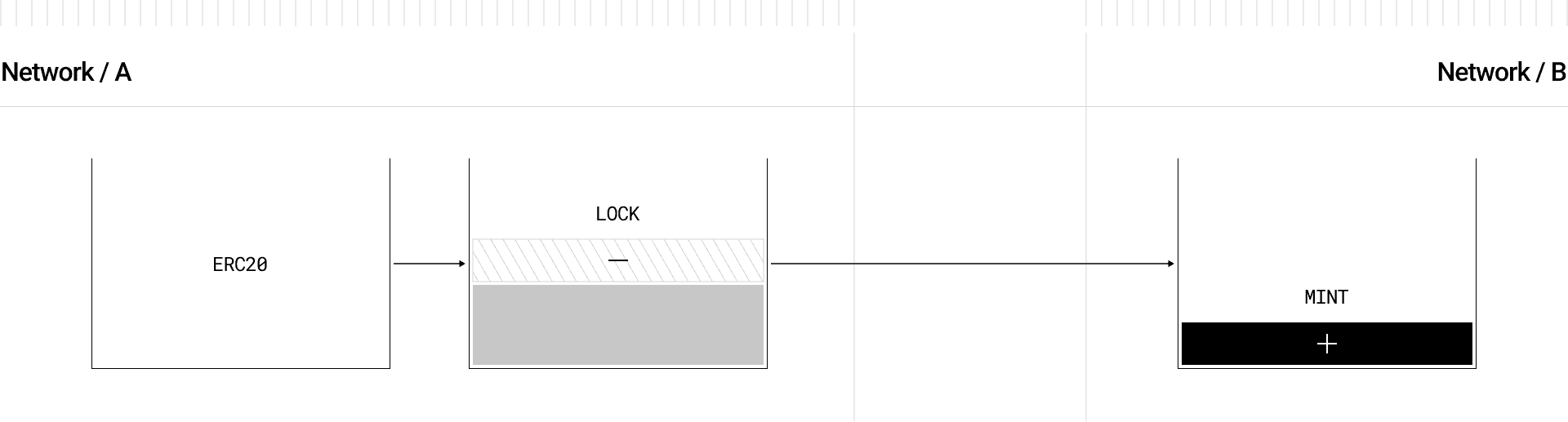
Source: LayerZero Docs
Positives: Allows any existing token to become "omnichain" without needing modification to the original token contract.
Drawbacks: This model introduces custodial risk in the adapter contract, where the original tokens are locked. The newly issued token on the destination chain is not truly native (e.g., lzUSDC), which becomes an efficient but risk-elevated form of wrapping.
Risk Assumptions: This model again relies on the integrity of LayerZero's messaging infrastructure. Smart contract security of the Adapter contract, where the original token is held, becomes an additional risk consideration. In turn, this introduces liability of the liveness in the source chain hosting the Adapter contract, which is the backing of all the OFTs being minted cross-chain. Finally, this setup makes the asset security becomes dependent on the operational risks of both the source and destination chains, therefore making the rehypothecation risk an important detail.
#3. Other Systems
While LayerZero's dual-model approach offers significant flexibility, it operates within a competitive landscape of alternative bridging solutions. Each alternative presents a different architecture with unique trust assumptions and trade-offs, which are crucial to understand for a comprehensive risk assessment. The primary models in the market include traditional wrapped bridges, platform-specific canonical bridges, and other interoperability protocols like those from Circle and Chainlink.
#3.1 Traditional Wrapped Bridges
Traditional wrapped bridges operate on a straightforward lock-and-mint model. When a user wants to move an asset from a source chain to a destination chain, they lock their original tokens in a smart contract controlled by the bridge provider on the source chain. The bridge's off-chain infrastructure detects this deposit and proceeds to mint a corresponding "wrapped" or synthetic version of the token on the destination chain.
The core issue with this model is that control over the locked, canonical assets rests entirely with the bridge provider, creating a significant custodial risk and a central point of failure. This design also leads to a problem of liquidity fragmentation, as different token versions of the same underlying asset are interacted with as independent tokens, complicating the user experience and fracturing market depth, also requiring an additional step to wrap/unwrap tokens on the source chain.
#3.2 Canonical Bridges
Canonical bridges are the official bridges built by Layer 2 teams or foundations to connect their ecosystem directly to a Layer 1, most commonly Ethereum. Examples include the Arbitrum Bridge and the Optimism Bridge. These bridges typically use a lock-and-mint mechanism for assets moving from L1 to L2 and a burn-and-unlock mechanism for the return trip. Their primary advantage is security; instead of relying on a small set of external validators, they inherit the security of the underlying L1 through the L2's native validation mechanism, such as fraud proofs (for optimistic rollups) or validity proofs (for ZK-rollups). However, this security often comes at the cost of speed and convenience, as withdrawals from optimistic rollups can be subject to long challenge periods (e.g., seven days). Furthermore, these bridges are purpose-built and not designed for general-purpose interoperability between any two chains.
#3.3 CCTP (Circle)
Circle's Cross-Chain Transfer Protocol (CCTP) is a specialized burn-and-mint protocol designed exclusively for native USDC. When a user transfers USDC, the protocol's contracts initiate a burn on the source chain. Circle's off-chain services observe this event, and upon verification, authorize the minting of an equivalent amount of native USDC from the official contract on the destination chain. This process eliminates wrapping and fragmentation, ensuring the asset is always canonical USDC. The entire system's integrity relies on trusting Circle as a centralized, regulated entity to securely manage the minting and burning process. While this offers high capital efficiency and a seamless user experience, it is a closed ecosystem limited to a single asset and relies entirely on a single, trusted counterparty.
#3.4 CCIP (Chainlink)
Chainlink's Cross-Chain Interoperability Protocol (CCIP) provides a generalized framework for cross-chain messaging and token transfers, supporting both burn-and-mint and lock-and-mint models. Similar to LayerZero's OFT, Chainlink's solution allows token issuers to maintain control over their canonical token contracts across different chains. The primary architectural difference lies in the security model. CCIP's security is anchored by Chainlink's established Decentralized Oracle Networks (DONs), which are curated committees of highly reputable node operators responsible for validating and signing cross-chain transactions. This is complemented by a separate Risk Management Network that monitors for malicious activity. While this provides a robust security framework, it relies on the integrity of Chainlink's specific network of operators rather than a user-configurable set of verifiers.
#3.5 Comparison
When comparing these systems, the primary trade-offs revolve around four key dimensions: issuer control, security model, custodial risk, and flexibility. LayerZero's OFT standard and Chainlink's CCIP are notable for positioning the token issuer at the center of their design, granting them direct control over their token's cross-chain representation. This stands in stark contrast to traditional wrapped bridges and Circle's CCTP, where control is ceded to a third-party service provider.
The most critical differentiator, however, lies in the security and trust assumptions. Canonical bridges offer the highest level of security by inheriting it directly from the L1, but at the cost of limited flexibility. CCTP and traditional bridges centralize trust in a single entity or a small validator set, creating a single point of failure. Chainlink's CCIP relies on a robust but fixed set of curated Decentralized Oracle Networks (DONs). LayerZero's OFT standard is unique in its modular approach, allowing applications to define their own security by selecting a custom set of DVNs. This offers unparalleled flexibility but also transfers the responsibility of proper configuration—and the associated risk—directly to the application developer.
#4. Risks
#4.1 Smart Contract Risk
All LayerZero OFT smart contracts have been heavily audited by multiple third-party blockchain security firms. The latest audit done by Zellic confirmed no issues found in the contracts. The EndPointV2 contracts have been audited by seven different firms, and all the issues were either resolved or acknowledged.
The LayerZero Endpoint contracts, which are the entry point for sending and receiving cross-chain messages, are non-upgradable and permissionless. In addition, LayerZero has a $15M bug bounty program live on Immunefi since May 17, 2023. Both of these security measures lead the industry standard and help to proactively mitigate smart contract risks.
#4.2 Price Feed Risk
OFTs themselves do not inherently rely on or provide price feeds. However, if protocols using OFTs depend on third-party price feeds to determine collateral value, they may be exposed to risks arising from non-synchronized cross-chain data. This can lead to exploits such as borrowing cheaply on one chain and selling at a higher price on another, due to pricing discrepancies caused by latency in relayed information.
The Worker (DVNs and Executor) uses a priceFeed variable within the sending libraries, but this is specifically for managing up-to-date pricing related to transaction fees, such as accepting payments in the source chain's native token, or for handling service costs and ensuring consistent fee structures. This pricing data is unrelated to the valuation of OFT tokens within DeFi protocols.
#4.3 Dependency Risk
#4.3.1 Off-Chain Workers
In the LayerZero V2 protocol, Workers is the collective term for two key types of service providers: Decentralized Verifier Networks (DVNs) and Executors. Both are essential for enabling cross-chain messaging and execution by providing verification and execution services. DVNs verify the authenticity and correctness of messages or transactions across chains, while Executors carry out actions that require gas or computational resources on behalf of applications once verification is complete. Developers have the flexibility to choose among different Executors, including the default provided by LayerZero Labs, custom Executors built in-house or by third parties, or to opt out of automated execution entirely and manually trigger the necessary functions.
The DVN operates a single off-chain workflow that involves listening for the PacketSent event, verifying the packet’s payloadHash, and performing an idempotency check. The Executor performs two off-chain workflows: the Committer listens for the PacketSent event, and the Executor listens for the PacketVerified event and also performs an idempotency check. The MessageLibManager.sol contract is used by EndpointV2 to configure and manage these off-chain Workers.
#4.3.2 Third-Party Components
Currently, there are 49 Decentralized Verifier Networks (DVNs) available for applications to choose from when configuring their security stack. An application’s security stack refers to its unique combination of DVNs, Executors, and other security settings. DVNs are responsible for verifying messages sent across chains by applications using LayerZero.
The core principle of the security stack is the "X of Y of N" model. This means that to verify a message, a consensus must be reached by any Y DVNs, including X specific DVNs, selected from a total pool of N DVNs. Anyone can create their own third-party DVN, providing developers with a wide range of options tailored to their project’s needs. For example, a simple 1/1/1 security stack might be chosen for low-cost transfers, while a more robust 5/10/15 configuration could be used for high-stakes scenarios like DAO governance, which requires more verifiers and incurs higher costs.
To maximize security, applications can combine DVNs that reduce the risk of collusion or hacks by mixing centralized entities like Google Cloud with decentralized ones such as the Axelar DVN. The verification methods employed by these DVNs vary widely, including zk-technology, middlechains, consortium signers, and third-party bridges, each with different security profiles. A notable example is the new USDT0 token, developed in collaboration between Tether and LayerZero, which has its own dedicated DVN active on supported chains. Additionally, block confirmation settings are configurable to protect against chain reorganizations by requiring a specified number of block confirmations before verification occurs.
#4.4 Counterparty Risk
#4.4.1 Access Control Risk
The following contracts power LayerZero V2 on Ethereum Mainnet:
-
EndpointV2 serves as the primary entry point responsible for managing cross-chain communications.
-
SendUln302 is an Ultra Light Node (ULN) message library used for sending cross-chain messages.
-
ReceiveUln302 is a message library for receiving cross-chain messages.
-
SendUln301 is a send message library version compatible with EndpointV1, providing backward compatibility with EndpointV2.
-
ReceiveUln301 is a receive message library version compatible with EndpointV1 for backward compatibility with EndpointV2.
-
ReadLib1002 is a custom send library used to request and retrieve on-chain state from supported blockchains.
-
LZ Dead DVN is a placeholder DVN contract used during DVN provider configuration.
There is a sole entity with contract modification options on Ethereum Mainnet, LayerZero Multisig Wallet, a 3-of-5 threshold Safe that controls all the contracts listed above.
While third-party Workers (DVN and Executor) can be setup, LayerZero provides its own set of workers for applications to use:
-
LZ DVN is the Decentralized Verifier Network operated by LayerZero Labs, using a role-based access control system with roles such as
ALLOWLIST,DENYLIST,ADMIN_ROLE, andMESSAGE_LIB_ROLE. -
LZ Executor is responsible for automatically executing received cross-chain messages with a specified fee.
#4.4.2 OFT Ownership
When deploying an OFT token contract, the deployer is initially set as the owner and can configure various administrative settings. Ownership can later be transferred to a more secure multisig wallet with timelocks. Importantly, the token project team retains ownership on both the source and destination chains. Since LayerZero Endpoint contracts are immutable, they cannot disable support for any chain where the OFT is deployed. Additionally, reliance on LayerZero can be further minimized by selecting different sets of Workers (DVNs and Executors) for cross-chain messaging.
#4.5 Rehypothecation Risk
Rehypothecation risk arises when collateral locked to back a bridged asset is used for other purposes, such as staking or lending, thereby introducing new risks not originally anticipated by the user. This risk is particularly relevant to the lock-and-mint model used by the OFT Adapter, where a pool of the original token is held in a contract on the source chain. While the standard OFTAdapter.sol contract does not natively support rehypothecation, the entity controlling the contract could potentially upgrade it or migrate the locked assets to engage in yield-generating strategies.
A prominent example of this risk materializing in the broader ecosystem was the controversial "Stake the Bridge" proposal for Polygon's PoS bridge. The proposal suggested staking part of the assets held in the bridge contract to generate yield for the Polygon treasury. This sparked significant community backlash, as users had bridged their assets on that particular chain with the expectation that it would remain idle and secure, not be exposed to the inherent risks of liquid staking, such as slashing or smart contract vulnerabilities in the staking protocol. The initiative also highlighted a critical governance risk: that the custodians of bridged assets might unilaterally alter the risk profile of the collateral, eroding user trust and confidence.
Therefore, for any OFT using the Adapter model, users must not only trust the security of the LayerZero messaging protocol but also place significant trust in the governance of the project that owns the adapter contract, assuming the risk that the underlying collateral will not be rehypothecated. This elevates the counterparty risk beyond smart contract integrity to include the ongoing operational and governance decisions of the token issuer.
#4.6 Legal & Regulatory Risk
#4.6.1 Legal Qualification of OFT Tokens
The legal nature attributed to an OFT generally mirrors the characterization its counterpart enjoys on a single blockchain—be that a utility token, a stablecoin, or another form of digital asset. The mere fact that a token employs the OFT architecture does not, by itself, confer a uniform legal status; rather, the applicable classification is dictated both by the token’s functional design and by the body of law prevailing in the jurisdiction from which the issuer conducts business.
In many jurisdictions the foundational point of reference is a virtual-currency or crypto-asset paradigm, treating the OFT as a digital representation of value capable of being stored, transferred, and traded across distributed ledgers. An OFT that primarily serves as a store or transmission of value across chains will therefore often be viewed through this lens.
Where the token is purpose-built to operate chiefly as a means of payment or medium of exchange, it may fall within the ambit of a “payment token,” as contemplated, for example, under Swiss or Singaporean regulatory frameworks, each of which imposes distinct compliance requirements upon such instruments.
Within the United States, an OFT that does not display the hallmarks of a security may instead be captured by the notion of a digital commodity, thereby bringing it under the supervisory remit of the Commodity Futures Trading Commission.
Conversely, when the token is offered or promoted in a manner that creates a reasonable expectation of profit derived from the efforts of a common enterprise, it can satisfy the elements of an investment contract under the Howey doctrine—or analogous tests elsewhere—thus triggering securities-law oversight.
#4.6.2 Regulatory Points of Focus
Although the OFT model preserves the economic rights embedded in the underlying token, it also introduces clearly identifiable service providers—namely the default oracle and relayer stack, DVN operators, and any front-end initiating transfers—each of whom may be construed by regulators as a Virtual-Asset Service Provider, a Money-Services Business, or a comparable regulated entity.
From the regulator’s vantage point, several structural elements of the OFT framework demand close scrutiny. First, the cross-chain architecture disrupts jurisdiction-bound assumptions underpinning many financial regimes. The OFT.sol contract extends OApp.sol and inherits the ERC-20 interface, meaning a single contract address represents identical tokens across multiple networks while maintaining a unified aggregate supply. As a result, the same asset exists simultaneously on every supported chain, complicating supervisory models premised on a geographically fixed locus of issuance.
Second, the burn-and-mint mechanism raises questions about the moment and place of issuance. Under prevailing documentation, a balance is burned on the originating chain (Chain A) and, through the paired OFT contract, a corresponding amount is minted on the destination chain (Chain B). Regulators may need to decide whether this sequence constitutes fresh issuance, an exchange, or a transaction that escapes conventional categorization.
Third, ownership and governance features constitute potential centralization points. Each OFT is deployed as an Ownable contract whose owner—typically the issuer’s multi-signature wallet—may appoint a delegate empowered to configure parameters and to “skip” inbound packets at discretion. These levers, which include setting cross-chain peers, adjusting security options, and suspending or amending token functionality, could attract heightened regulatory attention.
#4.6.3 Middleware Layer Legal Risk
Middleware actors occupying the oracle and DVN layer hold a critical, if sometimes overlooked, position. Because they collect fees, validate cross-chain messages, and are easily identifiable on-chain, supervisory bodies may treat them as intermediaries that receive, transmit, or safeguard value on behalf of users. Such a perspective would subject them to AML and CFT obligations, licensing regimes, operational-resilience standards, and potentially even rules governing securities market infrastructures. A sufficiently decentralised design may, however, mitigate the risk of being captured by these regimes.
#4.6.4 Additional Legal Risks
The omnichain presence of OFTs generates additional complexity. A single token can be subject to multiple—occasionally conflicting—regulatory frameworks, making it difficult to determine which jurisdiction’s laws govern any given transaction or custodial relationship. Reliance on sophisticated smart-contract logic also introduces ancillary liabilities: coding flaws, unforeseen cross-chain interactions, or failed deliveries can precipitate token loss or systemic disruption, potentially engaging both contractual and tortious theories of liability. Moreover, insofar as cross-chain messages embed user or transactional metadata, data-protection regimes such as the GDPR may apply. The immutable and transparent nature of distributed-ledger storage sits uneasily alongside rights to erasure and other personal-data protections, adding yet another layer of regulatory risk.
#5. Conclusion
The LayerZero Omnichain Fungible Token (OFT) standard presents a powerful framework for achieving cross-chain token fungibility, primarily through its burn-and-mint model which creates a single canonical asset across multiple networks. By granting token issuers direct ownership and control over their omnichain deployments, the OFT standard effectively mitigates the liquidity fragmentation and custodial risks inherent in traditional wrapped bridges. Its defining feature is the modular and configurable security stack, which allows applications to select their own set of Decentralized Verifier Networks (DVNs). This flexibility distinguishes it from competitors with more rigid, monolithic security models, offering a tailored approach to cross-chain trust.
However, this flexibility introduces significant trade-offs. The security of any OFT asset is directly dependent on the integrity and configuration of its chosen off-chain workers, placing the onus of risk management on the implementing application. The lock-and-mint Adapter model, while versatile, introduces distinct custodial and rehypothecation risks that are absent in the native burn-and-mint setup. Furthermore, the entire framework operates within an unsettled legal and regulatory landscape, where the cross-jurisdictional nature of OFTs and the role of intermediaries like DVNs present complex challenges. Ultimately, while the OFT standard is a significant advancement in interoperability, its safe adoption requires a sophisticated understanding of these architectural nuances and a diligent approach to managing its multifaceted risks.
Given these complexities, both protocols and end-users must adopt a proactive stance toward risk management. It is crucial to diligently evaluate the specific implementation of each OFT, distinguishing between the non-custodial burn-and-mint model and the custodial lock-and-mint adapter, and most importantly, scrutinizing the composition of its security stack. A configuration relying on a single, project-run DVN, for instance, reintroduces a centralized point of failure, regardless of the underlying protocol's decentralization. Therefore, users and integrating protocols must carefully consider their preferred risk assumptions and actively control their exposure.
