An introduction to Nektar's Decentralized Infrastructure Marketplace
Classic shared security protocols act as trust marketplaces designed with capital providers on the supply side and users of that capital on the demand side, who use it to validate and secure their cryptoeconomic system. Although the restaking concept represents an advanced system that encourages growth and creates new usecases in the blockchain sector, some teething issues are starting to form:
-
The supply side already exists but the demand side is still in development which significantly lowers the "trust price"
-
A clear lack of "real yield" being passed to stakers
-
Centralized token allocation from LRT protocols and Node Operators
-
All protocol/projects are put into unified aggregation layers, which limits AVS growth
-
Each network has own unique requirements which cause higher costs for Node Operators
-
Risks stemming from implementation and parameterization
A potential solution to these challenges is presented by Nektar through its novel approach in connecting blockchain protocols with liquidity, infrastructure and experts. It meets these challenges by addressing the fact that capital and compute requirements vary vastly across projects and that each project also want to promote their own token. Nektar reshapes how aggregation layers work by making it easier to drive demand-side innovation while providing a sustainable and truly decentralized system for allocating resources while mitigating fragmentation.
Nektar operates as a Decentralized Infrastructure Marketplace (DIM) that serves as the exchange point for distributed network resource allocation across a wide spectrum of services: computational power, storage, node certification, advertising slots, DeFi yield sources, and many more usecases where “rented trust” through shared security represents just one of many possible usecases. At its core, Nektar utilizes 'Decentralized Asset Managers' (DAM) as a core architectural component. These DAM vaults are operated by specialized Managers who bring domain-specific expertise to their respective infrastructure services, leading to optimized performance and efficiency within each vault's designated function.
#Protocol Architecture
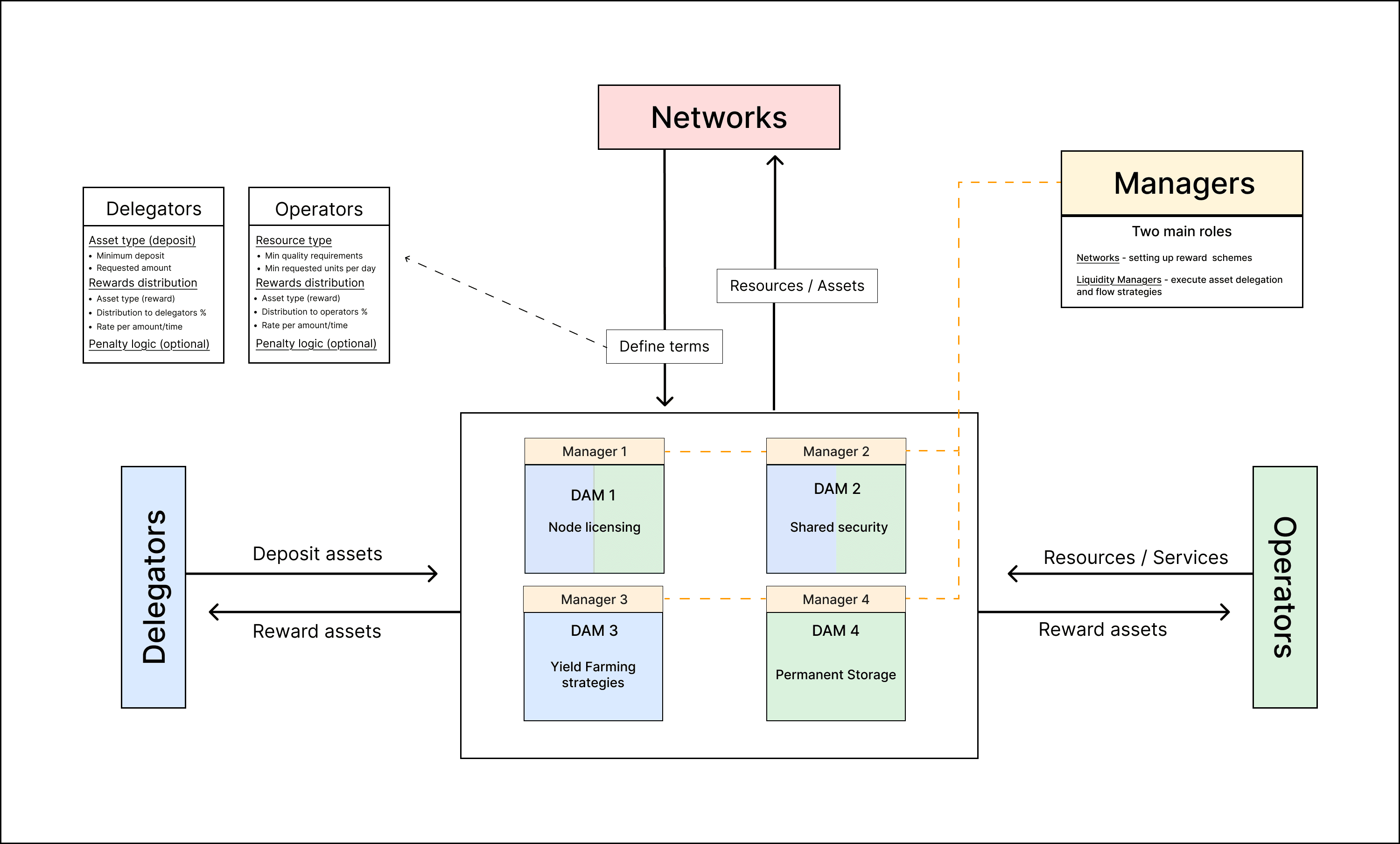
Nektar is a Decentralized Infrastructure Marketplace (DIM) platform that utilizes a non-layered, modular architecture strategically aligned with market supply and demand mechanics. The core and sole protocol components are the Distributed Asset Manager (DAM) vaults, each configured according to Network requirements and operated by Managers in a highly specialized manner.
Source: LlamaRisk
#Distributed Asset Managers: a liquidity aggregation solution
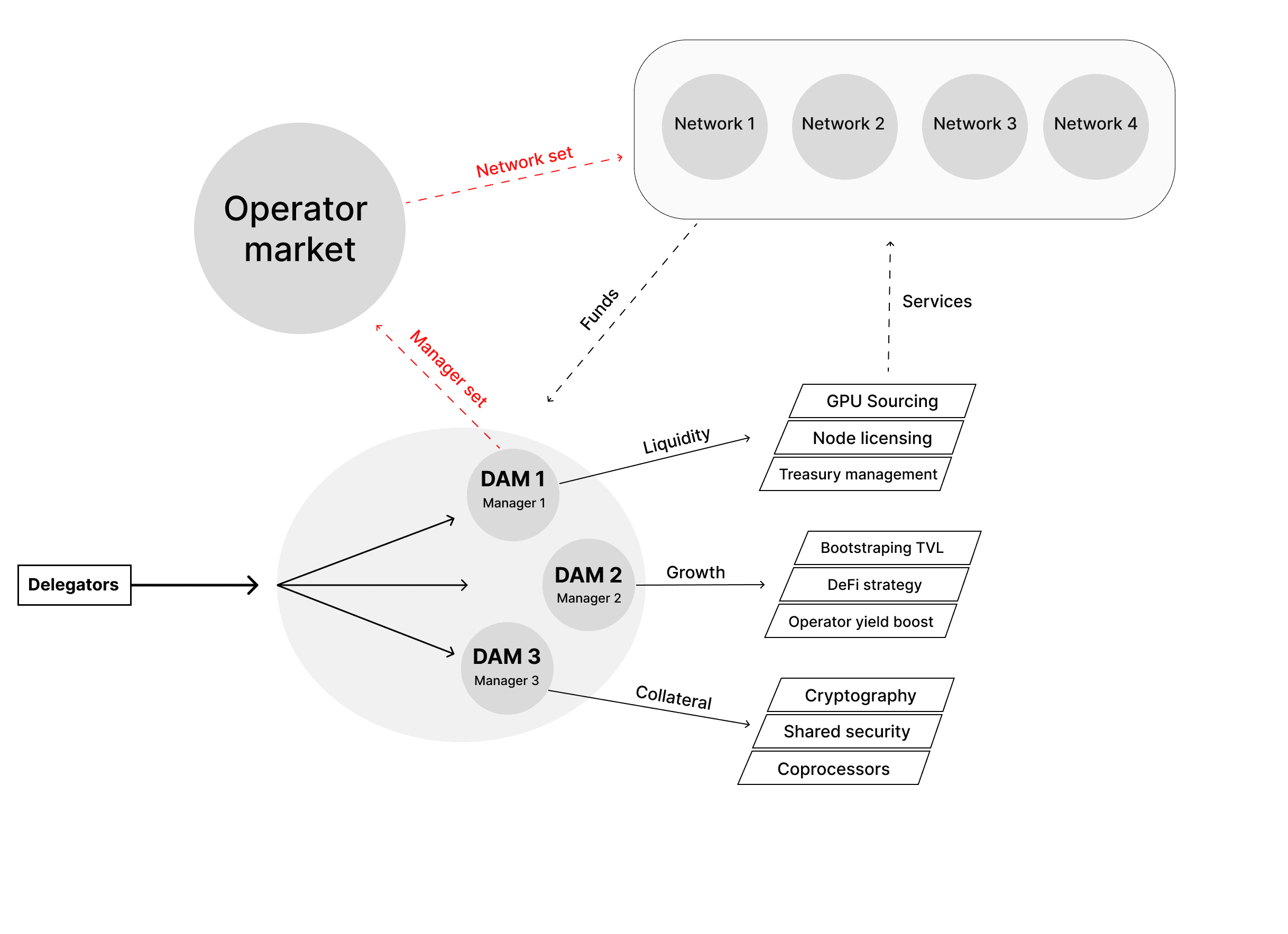
Nektar provides aggregated liquidity by connecting Delegators and Operators to Networks through Distributed Asset Managers (DAMs). DAMs are strategy management vaults configured by specific Network requirements and managed by expert(s) from required fields: Managers. DAMs also work to connect Operators with infrastructure that benefits Networks.
Distributed Asset Managers (DAMs) play a central role in token management activities, allowing projects to delegate assets for various uses like liquidity generation or running nodes. DAMs provide Networks the flexibility to drive specific outcomes, whether that’s attracting new operators or optimizing infrastructure to generate higher rewards.
Anyone can set up a DAM — from liquid shared security protocols and risk managers to syndicates, operators, or existing Networks. The creator of the DAM can define key parameters such as the lock-up period for assets, fees to be collected, and the intended use of the deposited tokens. In Nektar, using tokens as collateral is an option and not a requirement.
Source: LlamaRisk
This architecture allows Networks to establish their own parameters and implement their own reward schemes, either by onboarding new Operators or leveraging their existing operator set to create DAMs.
The DAM vaults function as isolated operational components of Nektar marketplace, which makes the system scalable and creates a foundation for positive value intra-network economics. The system design achieves scalability by allowing for the creation of additional DAM vaults as demand increases. The main intra-network (intra-protocol) value mechanism is twofold:
-
Cross-DAM activity in cases where specific Network use more than one DAM vault and,
-
Cooperation between DAM vault providers (Managers, Networks and Operators), where cooperation creates new Network.
#Decentralized Concentration Economy
The Decentralized Concentration Economy (DCE) is an economic model that addresses the limitations of shared security and aggregation by allowing projects to retain their tokens and unique implementations while benefiting from shared incentives. This model boosts capital efficiency through network collaboration without sacrificing project autonomy.
Shared security is highly effective in optimizing capital utilization, but it can be problematic due to the varying security requirements across different projects. Operators providing validation services to Network or Active Validated Services (AVS) often face increased resource demands as these implementations grow in complexity. Existing aggregation layers, such as Polygon’s, attempt to solve this by sharing security within their ecosystem but enjoy limited current adoption.
Nektar proposes the DCE economic model as a solution to these challenges, offering a decentralized and adaptable approach. Compared with other network-specific aggregation solutions, the DCE offers a more inclusive framework, addressing scalability and interoperability concerns in a way that is more attractive to a wider range of decentralized projects.
#Decentralized Infrastructure Marketplace
The Decentralized Infrastructure Marketplace (DIM) is a platform that connects all Network participants within a modular decentralized economy to efficiently aggregate liquidity, optimize infrastructure use, and implement customized reward schemes. It allows token holders to delegate their assets, which are then used to enhance infrastructure operations for various projects.
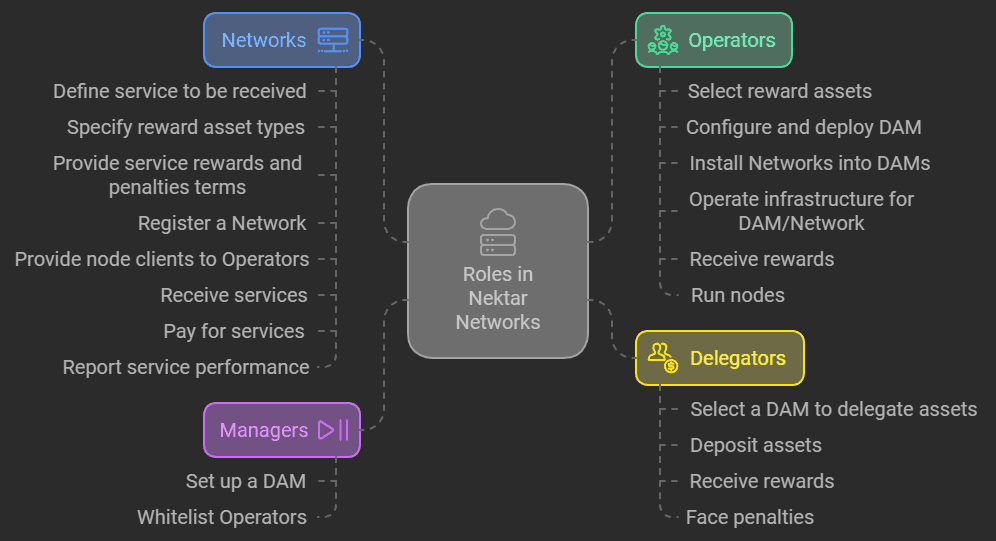
DIM ecosystem participants are:
-
Networks: the demand side of the marketplace; projects that aim to incentivize liquidity, attract new operators, or boost the loyalty of existing ones.
-
Operators: hardware providers and cloud managers (or software managers) focusing primarily on optimizing infrastructure and software environments. Their main goal is to efficiently manage nodes, ensuring consistent uptime and reliability.
-
Delegators are token holders looking for higher rewards they can get on their assets. Delegators need to select DAM(s) that fit their risk-reward preference.
-
Managers are actors who set up and whitelist Operators for DAM and manage resource allocation in DAM vaults. After setting up a DAM, a Manager can define essential vault parameters and whitelist specific Operators to join their DAM.
Source: Nektar documentation
In Nektar's marketplace, operators and delegators can join permissionlessly but networks and asset types must be whitelisted. The matchmaking process involves operators selecting Networks to install into Decentralized Asset Managers (DAMs) and delegators choosing DAMs to delegate assets to, enabling the flow of liquidity, security, and incentives. Networks pay rewards to operators and delegators based on predefined criteria, including asset type, deposit amount, and operational time. Metrics such as Global Traded Volume (GTV) and active daily users are used to measure platform growth, rather than TVL, which benefits the networks interacting with Nektar.
#Networks Use Cases
Nektar, as previously mentioned, offers a broad range of use cases as a marketplace. Currently, the main use cases are infrastructure and liquidity exchange. Network requirements can vary significantly, from cases where the primary need is computational resources (infrastructure), in which operators are the counterparties, to cases where the sole requirement is liquidity, in which the Network directly interacts with capital delegators without involving operators. These examples illustrate that Nektar’s DIM is highly adaptable, accommodating different participants and needs. The four main groups of use cases for Networks are as follows:
#1. Infrastructure
Infrastructure use cases focus on providing computational resources and network support without necessarily involving asset transfers. These scenarios cater to networks that primarily need additional computing power, storage, or other infrastructure-related services. Some infrastructure usecase examples:
-
Distributed Computation: a Network requiring additional processing power for complex calculations, data analysis, or AI model improvements.
-
Decentralized Storage: a Network needing secure, distributed storage solutions for large datasets.
-
Node Operation: Providing validators or full nodes to support network operations and consensus mechanisms.
#2. Liquidity
Liquidity use cases involve the transfer of assets to time-locked vaults, which are then used in a non-custodial and transparent manner as proposed by the Network. These scenarios are designed for networks that require capital injection or liquidity support. Examples include:
-
DeFi Liquidity Pools: Providing liquidity for decentralized exchanges or lending platforms.
-
Yield farming strategies: Networks can source liquidity to implement advanced yield generation strategies. To attract Delegators who will provide liquidity, Networks can offer these.
-
Staking incentives: To attract delegators, Networks can offer some special rewards or incentive structures for their staked assets.
#3. Growth
Growth use cases involve asset transfers to time-locked vaults, in a different way to liquidity scenarios, the Network can withdraw these assets once the lock expires. These funds do not return to Nektar and are typically used for network expansion and development. Some examples:
-
Node license sale: Networks can sell node licenses for operators and in that way generate income (funding, additional income) while also expanding the validator base.
-
Operator yield boost: Networks can provide additional rewards for operators with specific performance and reliability criteria.
#4. Shared Security
In shared security scenarios, assets remain within Nektar as collateral. This model allows Networks to request assets if Operators behave maliciously, with funds moved to a time-locked vault for dispute resolution. These usecases are equivalent to shared security, and the main purpose is to provide Network stability and security. Usecases may involve rollups, coprocessors, cryptography, MEV management, and other ideas such as proofs, execution environments, oracles, sidechains, or offchain infrastructure.
These use cases demonstrate the versatility of Nektar's Decentralized Infrastructure Marketplace (DIM), accommodating a wide range of network requirements from pure infrastructure needs to complex financial operations and security mechanisms.
#Website Operator
Nektar’s website is operated by Nektar Foundation, which claims to be composed of core contributors to the development of Nektar. The foundation explicitly states that it does not seek to directly or indirectly manage, control, or influence Nektar in any way. The website is designed for informational purposes only, and accessing or using it does not establish a contractual agreement with the Nektar Foundation. The foundation asserts not to make any offerings or solicit any services through the website and makes clear that is not representative of the community in any way.
Additionally, while integrations or initiatives regarding LRT vaults creations or Network enabling may be discussed and finalized with the Nektar Foundation or its affiliates, such information is not publicly communicated or integrated into binding terms.
#Nektar’s Competitive Advantage
Nektar has no direct competitors in the shared security sector and is, moreover, complementary to most protocols within the shared security and LRTfi space. Key differences between Nektar and shared security protocols include:
#Broader Target Market
The Nektar protocol targets a larger market by supporting the exchange of nearly all types of distributed resources, whereas shared security protocols focus exclusively on the exchange (or sale) of economic security.
#Fairer Market
The Nektar protocol achieves better market prices (fair pricing) for distributed resources because Networks initiate the exchange process, and DAM configurations are tailored to Network requirements. In contrast, shared security protocols are creating a large supply, resulting in a significant imbalance with demand (i.e. low demand from AVSs).
#Decoupling proof of stake into liquidity
Nektar may allow for new levels of capital efficiency through redirecting traditionally unidirectional Proof of Stake yield to much more granular areas that DAMs perceive need additional support. This is a massive step forward in economic efficiency and one that may enable a plethora of Netkar-specific product market fit. All components of the Network remain intact but are used for other applications, thereby broadening opportunity.
#Permissionless participation
Nektar's permissionless design allows open participation from all stakeholders, including validators, delegators, and asset managers, without reliance on trusted parties. Delegators can directly deposit into the DAM vault of their choice without depending on LRT protocols' allocation strategies or operators' due diligence.
Comprehensive and Flexible Incentives System Nektar’s marketplace enables the Networks to rewards operators for additional duties and enables delegators more flexibility in capital allocation. Networks benefit from the opportunity to offer operators a competitive price for trust and a more robust incentive structure.
#Dynamic Asset Management Scenarios
On Nektar DIM, Networks can implement a variety of asset management strategies through the Decentralized Asset Managers (DAM) vaults, tailored to meet specific needs such as liquidity, growth, collateral, stability funds, pooled insurance, yield optimization, and so on. Each DAM vault is managed by an assigned expert or a team of specialists, each bringing deep expertise tailored to the specific focus area of the vault.
Nektar in its early development stage targets core issues faced by existing shared security protocols like EigenLayer and Karak. It offers solutions that address those protocols’ limitations, particularly in terms of decentralization, capital efficiency, flexibility, knowledge specialization, and in general better conditions for all participants. However, it's important to note that Nektar has not yet been battle-tested (whether battle-tested shared security protocols yet exist is a matter of debate). While its approach shows promise in addressing the current challenges, it is too early to provide fully objective conclusions - only well-informed opinions based on its design and potential.
#Conclusion
Nektar presents itself as a multi-functional marketplace capable of supporting decentralized services across the blockchain sector. The platform's design serves a wide range of use cases, such as distributed infrastructure optimization, providing liquidity, shared security, and in general matching blockchain networks with critical resources for their functionality. This expansive scope positions Nektar as a potential solution for the main problem in blockchain space - collaboration across decentralized ecosystems.
In the context of restaking, Nektar prioritizes flexibility by allowing Networks to implement consensus mechanisms, incentive structures, and business models tailored to their unique requirements. By addressing early-phase market inefficiencies, such as demand-side imbalances and centralized resource allocation, Nektar creates a more sustainable and adaptable environment for their growth and further development.
The introduction of Decentralized Asset Manager (DAM) vaults, operated by specialized Managers, reflects a forward-thinking modular architecture. This approach could unlock vast potential by enabling domain-specific expertise and targeted solutions within the marketplace. However, questions about the operational scope of Managers and the scalability of this structure are still open. These factors will play a critical role in determining the system’s effectiveness as adoption increases.
Despite its early development phase, Nektar has successfully identified the core limitations of existing restaking protocols and proposed innovative solutions to address them. While the theoretical framework shows promise, its practical viability will depend on the ability to achieve widespread adoption, scalability, and consistent performance.
